What a learning curve.
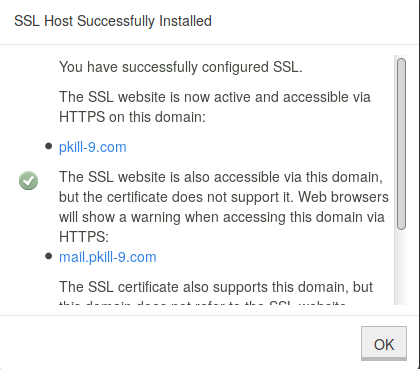
If you will notice, pkill-9.com is now secured via secure sockets layer. Thanks to namecheap.com. It was $9/year for an ssl certificate through name cheap, vs $75 through godaddy. Interesting learning process.
Thanks for your Patience!
Wayno